Results 1 to 1 of 1
-
10th Jul 2014, 03:57 PM #1
 BrutPOS Botnet Scans for Weakly Protected RDP Servers
BrutPOS Botnet Scans for Weakly Protected RDP Servers
Reports from security researchers show that an army of thousands of infected computers is used by cybercriminals to detect point-of-sale (POS) terminals that are accessed via the remote desktop protocol (RDP) with credentials that can be cracked through brute-force attacks.
Earlier today, security company IntelCrawler presented a report showing that cyber-crooks compromised computers that were used to scan for specific IP ranges in an attempt to find POS software that could be accessed through RDP.
FireEye also published an analysis, with more details about the botnet including 5,622 machines in 119 countries, which they called BrutPOS, and about how it is operated by the threat actors.
At the moment, information on how the malware is distributed is not complete, but the company detected the destre45[.]com website as one of the attack vectors. Researchers assume that other distribution methods may rely on services provided by other cybercriminals.
After infecting the computer, the malware connects to a command and control (C2) server and receives a dictionary with usernames and passwords to be used for the brute-force attack. A list of IP addresses to be scanned is also provided.
Then, it proceeds to check if the port used by the remote desktop protocol (3389) is open on any of the systems in the given IP range. Should it find an open connection, the brute-force attack begins, and in case of success, the credentials are sent immediately to the C2 server.
FireEye said that it detected a number of five C2 machines, and only two of them, which seem to have been set up recently (one towards the end of May and the other in early June), are currently active.
Both of them are located in Russia, on the THEFIRST-NET network. Other control systems were located in Iran and Germany.
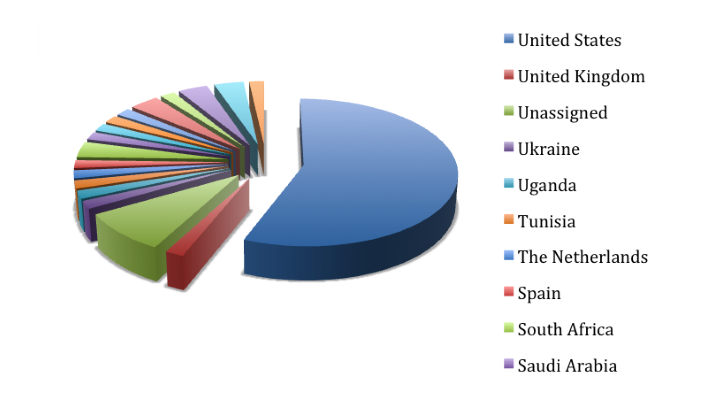
According to the company’s analysis, the attackers specified a set of 57 IP address ranges, 32 of them located in the United States. Additional countries include United Kingdom, Netherlands, Spain, Tunisia, South Africa, Saudi Arabia, Uganda, and Ukraine.
By gaining access to the command and control servers, FireEye researchers found information about the RDP servers that were labelled as an asset by the cybercriminals.
It appears that they found 60 machines, 51 of them being located in the U.S.; the most used username/password pairs were “administrator” (36 cases) and “pos” and “password,” each occurring in 12 cases.
This is not the first time that security researchers bump into this botnet, as it was also reported back in March, while the brute-forcing component was discovered in February. However, too little information was available at that time.
Based on its findings, FireEye notes that the attackers are most likely from Russia or Ukraine.Kepler Reviewed by Kepler on . BrutPOS Botnet Scans for Weakly Protected RDP Servers http://i1-news.softpedia-static.com/images/news-700/BrutPOS-Botnet-Scans-for-Weakly-Protected-RDP-Servers.jpg Reports from security researchers show that an army of thousands of infected computers is used by cybercriminals to detect point-of-sale (POS) terminals that are accessed via the remote desktop protocol (RDP) with credentials that can be cracked through brute-force attacks. Earlier today, security company IntelCrawler presented a report showing that cyber-crooks compromised Rating: 5
Sponsored Links
Thread Information
Users Browsing this Thread
There are currently 1 users browsing this thread. (0 members and 1 guests)
Similar Threads
-
[Other] High performance RDP server for 8 persons
By ashokbansal in forum ArchiveReplies: 2Last Post: 1st Apr 2012, 09:08 AM -
How many of you are interested for a EU RDP server?
By LEVAC109 in forum Polling PlazaReplies: 7Last Post: 11th Feb 2011, 11:21 AM -
[Other] RDP server slot for uploading
By samipk in forum ArchiveReplies: 0Last Post: 29th Sep 2010, 05:33 AM -
Looking for a semi-dedicated server.
By G56Ace in forum Hosting DiscussionReplies: 3Last Post: 18th Jan 2009, 03:21 AM -
ISP Says RIAA Must Pay for Piracy Protection
By DJ Norix in forum News & Current EventsReplies: 3Last Post: 14th Jan 2009, 08:34 PM













 Register To Reply
Register To Reply





 Staff Online
Staff Online
themaLeecher - leech and manage...
Version 4.94 released. Open older version (or...